rC3: Massive vulnerabilities in apps from mobile network providers
Source: Heise.de added 30th Dec 2020Florian Schweitzer presented his personal collection of vulnerabilities in the area of Cross Site Request Forgery (CSRF) in web applications of Austrian mobile phone providers at the remote Chaos Communication Congress (rC3). The hackers described the security gaps, also known as “session riding” or “sea surf”, and the attacks based on them as “particularly dramatic” because they were “very easy to exploit”.
Simple attack, difficult to detect Unlike attacks on the Signaling System 7 (SS7) used in 3G, there are no CSRF Access to a gateway and no know-how about network operation required, the hacker explained. Sea surfing attacks could start with a “boring, annoying newsletter”. A click on an allegedly redeeming “Unsubscribe” link contained therein is often sufficient for an intruder to set up a call diversion for a target person. This also enables the passwords of e-mail accounts with providers such as Google, Yahoo or Microsoft that are linked to the phone number to be reset and the accounts to be adopted.
When unsubscribing from a newsletter, only a website appears on the user’s screen, after which one has successfully unsubscribed, Schweitzer explained the procedure. If you then try to log into your e-mail inbox, you are locked out. Anyone who then connects to the called up link can possibly see a form with two invisible fields in the source code of the page that pops up.
One of them is directed to the site of the mobile phone provider, where a new telephone number is automatically entered and the call diversion is set in the background, the activist reported. An invisible iframe is loaded and automatically sent when the link is opened. Google and other e-mail providers also persuade users to supposedly store a mobile phone number to protect their account in order to prevent forgetting a password. Such an account can also be reset.
No new problem According to Schweitzer, CSRF in itself is nothing new and has already been described as a “confused deputy” problem in the 1980 er. In principle, one program with fewer privileges will get a second with more rights to do something. The authentication can also be done with IP addresses. The attacker sends a link and thus induces the user to visit a compromised page. This sends a get request and receives the payload back in the form of a form. This is sent to another site where the target person is already authenticated. The server then believes that the victim has sent the command or the request and is taking the desired action.
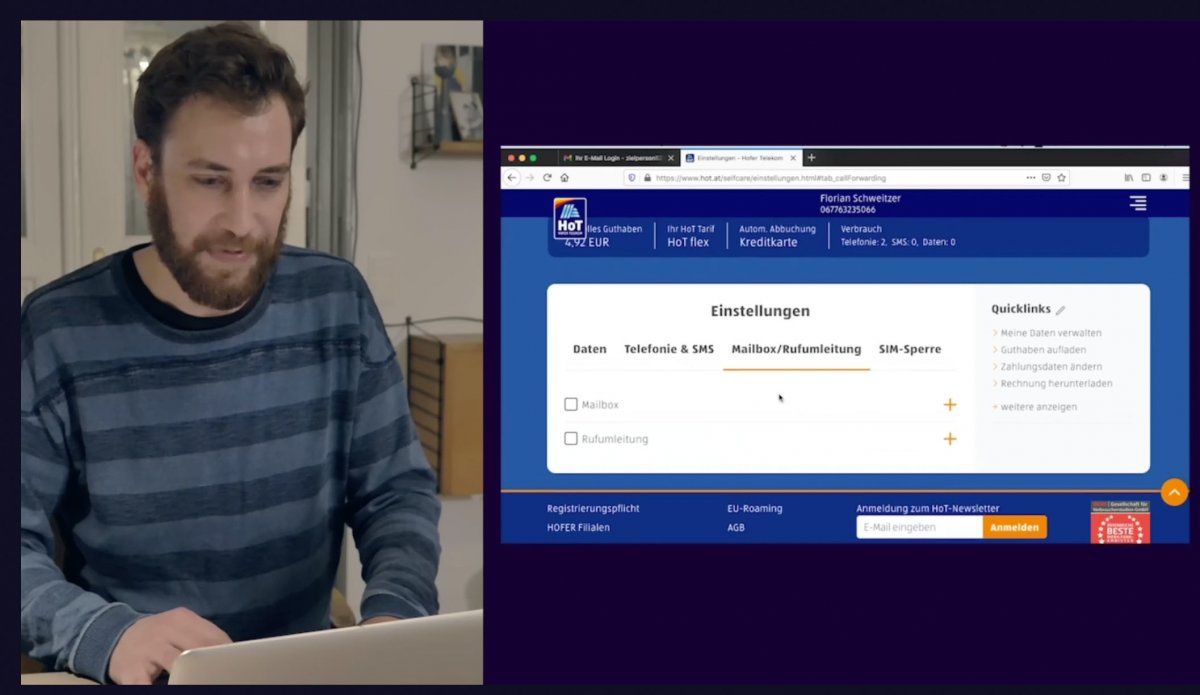
In demos, the security expert demonstrated how relevant loopholes at Austrian providers can be exploited. Ventocom, a provider that enables third parties to operate their own mobile phone brand, has proven to be vulnerable. Rapid Mobile, a Linz cable operator and Aldi-Süd subsidiary Hofer Telekom (HoT) make use of this offer. The latter alone has issued over a million SIM cards in Austria and around a hundred thousand in Slovenia.
The customer login to hot.at is password-free using a PuK code, which can be sent by e-mail can leave. All kinds of changes can be made in the internal area, including the customer password. For this you have to enter the old one. If you enter a new e-mail address or set up call diversion, this is not necessary. The attacker can use a fake newsletter with the problematic link to enter an electronic mailbox controlled by him and receive an access link there.
Improved protection in Chrome Schweitzer also showed the next steps with call diversion, changing the password on Google over the phone and taking over a Gmail account. For hot.at, there is already a valid session cookie in the target person’s browser that opens access to the customer account. The post request running in the background via an iframe works with Safari, Firefox, Samsung Internet, Opera and Internet Explorer, where even phone calls can then be completely recorded. Chrome have introduced stricter rules for cookies in Mitte 2019 with the “SameSite attribute” and thus significantly improved protection against CSRF.
With the provider “Drei” the hacker came across a comparable vulnerability, which affected 3.9 million accounts in Austria. Anyone who accesses the Internet via the provider’s cellular network is immediately identified by their number and can always log into their account automatically. This leaves the choice between a valid session cookie and the default activated auto-login for the further procedure. A permanent account takeover and eavesdropping are not possible here, however, since logging in only works with a current click due to an implemented function against “clickjacking”.
Even with the A1 subsidiary Yesss, which operates as a Schweitzer found such gaps to act as a service provider for ten virtual mobile phone providers, such as the newspapers Kurier and Krone, as well as an energy supplier. This affected over 5.4 million customers. Since he – in contrast to the other providers – has found a contact person for IT security here, the weaknesses have since been remedied after a hint from him. An attacker was even able to set a customer password for an entire number porting and, for example, read SMS and reset Twitter accounts. The web app from T-Mobile Austria (Magenta) was “safe”.
Dozens of million devices in Europe are vulnerable Schweitzer estimates that a total of 40 percent of Austrian citizens were (were) affected by the gaps. Across Europe there are likely to be tens of millions, as things look hardly any better there. Vulnerable endpoints could be identified in a short amount of time. Actually, it is forbidden in the EU to offer such attack surfaces in important infrastructures. Apparently the sanctions are too low and nobody is checking whether security standards are being met. A heise online reader recently noticed a vulnerability on the Vodafone Germany website that allowed a similar attack via “Reflected Cross-Site-Scripting”.
The expert recommends developers to use anti-CSRF To implement tokens, to set a strict “SameSite” rule and to require a password for important changes to account data. The “same-origin policy” of browsers does not offer any remedy. Users should not use their phone number to restore accounts, as mobile operators are “the weakest link in the security chain.” You should not log into important accounts with the standard browser, deactivate auto-logins and actively log out.
(mho)
brands: cellular CODE Google Microsoft Million Mobile New other Samsung Telekom Vodafone media: Heise.de keywords: App Google Internet Mobile Phone Samsung Server
Related posts
Notice: Undefined variable: all_related in /var/www/vhosts/rondea.com/httpdocs/wp-content/themes/rondea-2-0/single-article.php on line 88
Notice: Undefined variable: all_related in /var/www/vhosts/rondea.com/httpdocs/wp-content/themes/rondea-2-0/single-article.php on line 88
Related Products
Notice: Undefined variable: all_related in /var/www/vhosts/rondea.com/httpdocs/wp-content/themes/rondea-2-0/single-article.php on line 91
Warning: Invalid argument supplied for foreach() in /var/www/vhosts/rondea.com/httpdocs/wp-content/themes/rondea-2-0/single-article.php on line 91