l + f: Security nightmare SMB in the browser
Source: Heise.de added 07th Jan 2021Security purists have long warned against technologies like web assembly and web sockets. Now a hacker shows what is possible with it.
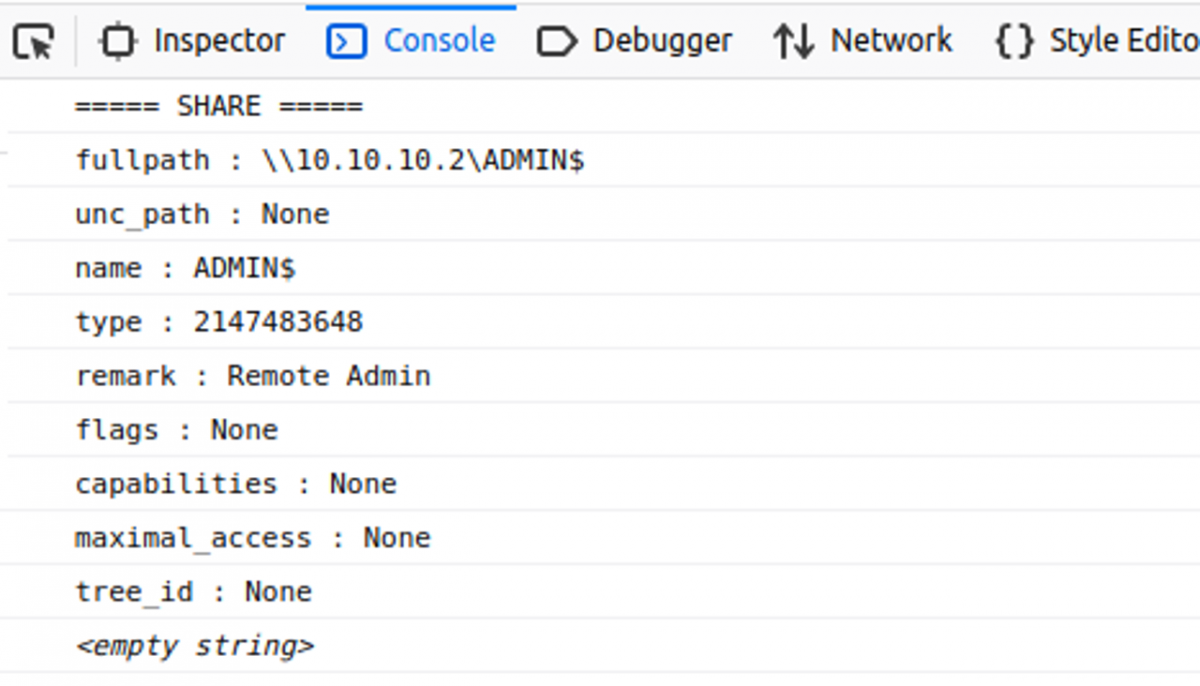
A hacker has a lot Effort implemented the proprietary Microsoft protocol for Windows networks (SMB) in web assembly. What initially appears to be a quirky tinkering project could have enormous effects on IT security. Because this is based on putting as many hurdles as possible in the way of attackers. However, one of these hurdles has been overcome.
Ultimately, this means SMB -Hack that an exploit of a browser bug could use it to directly access file shares and other resources in the Windows network. In other words: The exploit could talk directly to the SMB port 445 of the other Windows systems in the local network via websockets. So far, this required a detour via tools on the attacked computer, which is blocked by the browser’s sandbox, among other things.
(ju)
445
brands: local Microsoft other Quirky media: Heise.de keywords: Windows
Related posts
Notice: Undefined variable: all_related in /var/www/vhosts/rondea.com/httpdocs/wp-content/themes/rondea-2-0/single-article.php on line 88
Notice: Undefined variable: all_related in /var/www/vhosts/rondea.com/httpdocs/wp-content/themes/rondea-2-0/single-article.php on line 88
Related Products
Notice: Undefined variable: all_related in /var/www/vhosts/rondea.com/httpdocs/wp-content/themes/rondea-2-0/single-article.php on line 91
Warning: Invalid argument supplied for foreach() in /var/www/vhosts/rondea.com/httpdocs/wp-content/themes/rondea-2-0/single-article.php on line 91